As video becomes an integral feature in SaaS platforms, from internal training tools to global eLearning apps, developers are increasingly responsible for not just delivering video—but securing it. For platforms monetizing premium video content, piracy isn’t just a nuisance; it’s a revenue-killer.
While DRM (Digital Rights Management) handles encryption and playback rights, it can’t stop what’s become the most common source of leaks in 2025: screen recording and credential misuse. That’s why a new standard is emerging in video API architecture—session-based forensic watermarking.

What Is Session-Based Watermarking?
Session-based watermarking is a method of embedding unique, tamper-resistant watermarks into a video stream at the time of playback. These watermarks are generated using user/session-specific data such as:
- User email or ID
- IP address
- Session token
- Timestamp
- Device fingerprint
The watermark is dynamically injected into the video so that each viewing session produces a uniquely marked video stream.
If the video is leaked—whether via screen recording, download hacks, or internal sharing—the platform can extract the watermark from the leaked copy and trace it back to the exact user session.
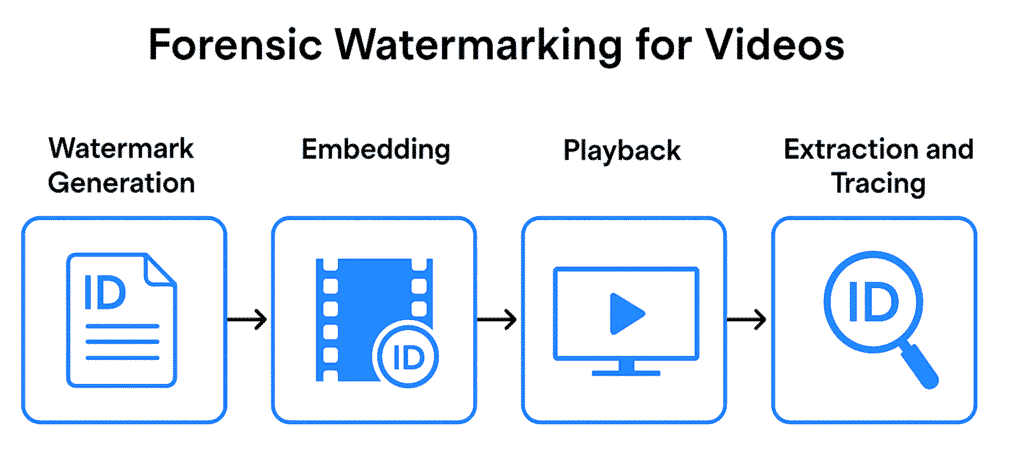
Why API-Driven Platforms Need It
Developers building custom platforms—whether LMSs, video conferencing tools, or SaaS-based training suites—often rely on video APIs to stream content securely. But a secure stream isn’t secure if you can’t audit abuse.
Session-based forensic watermarking offers developers a practical and scalable method to:
- Deter piracy by introducing accountability
- Monitor user behavior more intelligently
- Provide legally defensible evidence in copyright disputes
- Enhance trust for clients and educators using your platform
How It Works in a Video Delivery Pipeline
Here’s how a typical implementation looks within a secure video API system:
- User Authenticates: A user logs into the platform, starting a new viewing session.
- Session Token Generated: The backend creates a session token tied to user identity, IP, and device data.
- Video Request Initiated: The user clicks play. The front end requests a secure playback URL via the video API.
- Watermark Embedded Dynamically: A server-side or edge-side system encodes the watermark into the stream on-the-fly.
- Stream Delivered: The DRM-protected and watermark-embedded video plays on the user’s browser or app.
If a screen recording of that session leaks, the embedded watermark can be extracted using forensic tools and matched to the session metadata stored in the backend.

Visible vs. Invisible Watermarking in APIs
There are two types of watermarking used in SaaS video environments:
- Visible Watermarks: Overlays like user email, appearing dynamically on screen during playback. While video platforms focus on dynamic overlays, document security often requires different approaches, with tools like Watermarkly specializing in applying persistent watermarks to PDF files and static content. They can deter casual piracy but are easily cropped or obscured.
- Invisible (Forensic) Watermarks: Embedded into the video data at a pixel or signal level. They’re undetectable to the eye and persist through screen recording or re-encoding.
Most modern video API providers now support both types simultaneously, giving developers the best of both worlds—visible deterrence and invisible traceability.
Real-World Use Case: Secure LMS for Compliance Training
Imagine you’re building an LMS for financial institutions delivering high-stakes compliance training videos. These videos:
- Contain sensitive internal procedures
- Must be shared across offices globally
- Require strong audit trails for regulatory compliance
Here’s how forensic watermarking strengthens your architecture:
- Every employee watching the training gets a stream uniquely tagged to their login session
- If any video is recorded or shared, the watermark points to the individual responsible
- HR or legal can use this evidence internally or externally
- No need to rely solely on NDAs—technology enforces accountability
Without watermarking, a single leak could result in a compliance breach and major financial penalties.
Benefits for DevOps and Product Teams
Forensic watermarking isn’t just a security upgrade—it’s a product advantage. Here’s how it benefits teams building video-heavy applications:
1. Faster Piracy Response
Detecting a leaked video? Run it through a forensic extractor, find the user session, and shut down the offending account. No guesswork.
2. User Behavior Analytics
Correlate watermarked sessions with unusual patterns—like frequent IP changes, excessive views, or simultaneous logins.
3. Developer-Friendly APIs
Video Streaming Platforms like VdoCipher offer REST APIs and SDKs for watermark customization:
4. Scalability
Session-based watermarking works for platforms with 100 users or 100,000. It adds milliseconds to load time and runs smoothly alongside CDN delivery.

Limitations to Consider
While forensic watermarking is powerful, it’s not infallible. Developers should consider:
- Screen Recording Apps: While watermarking can trace leaks, it can’t prevent recordings by itself—pair with DRM and screen-capture deterrents.
- Storage Requirements: Watermarking doesn’t bloat file size, but storing session metadata requires secure, scalable logging.
- Legal Processing: To extract and act on a watermark, you need trained personnel or service-level support.
These are easily handled with the right platform (like VdoCipher), which bundles DRM, watermarking, analytics, and takedown support into one suite.
Future of Video Watermarking in Developer Workflows
As AI tools and generative video manipulation grow more accessible, even sophisticated pirates are experimenting with deepfake-style video edits to remove visible markers. Invisible, session-tied watermarks are a key line of defense against such manipulation.
In the future, expect:
- Edge-based watermarking for ultra-low latency streaming
- Watermark analytics dashboards for admin users
- Hybrid blockchain + watermark auditing for unalterable playback logs
These aren’t just security upgrades—they’re product differentiators that will shape which platforms content creators trust.
Final Thoughts
If your SaaS platform streams premium or proprietary video content, it’s time to think beyond encryption. Session-based forensic watermarking is the silent, scalable way to hold every user accountable—and future-proof your platform against the growing threat of content theft.
For developers, it’s easy to integrate. For users, it’s invisible. And for video protection, it’s indispensable.
- 3shares
- Facebook0
- Pinterest0
- Twitter3
- Reddit0













